September 19, 2023
Where and How are Cryptocurrencies Stored?
Cryptocurrencies are an important emerging asset class, however most legal and financial professionals don’t know enough about these assets to answer client’s questions meaningfully.
Cryptocurrencies are an important emerging asset class, however most legal and financial professionals don’t know enough about these assets to answer client’s questions meaningfully. The first step in understanding how cryptocurrencies can fit into a client’s plan is understanding where and how they are stored. We will go over the two key decisions clients make when deciding how to custody their digital assets, the pros and cons of each, and multiple custody solutions so you know what your client is talking about when they mention their ‘MetaMask’ or ‘cold storage device.’
We will explain how to inventory cryptocurrencies by providing examples of where and how the assets can be stored. Cryptocurrency owners are faced with two decisions when it comes to how they will store their assets: centralized vs. decentralized storage and hot vs cold storage. It is helpful to think of these options as existing on continuums, such that cryptocurrency storage solutions can be placed on a 2-axis grid as seen below:
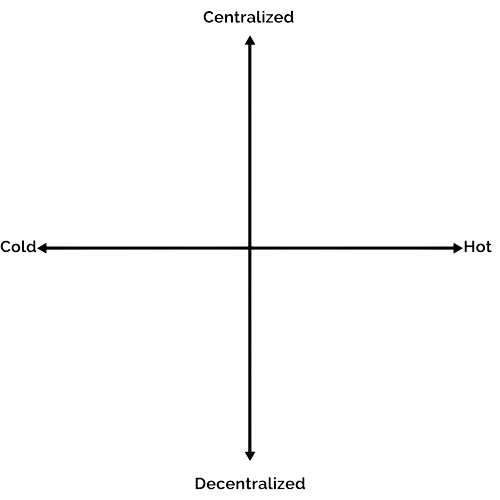
We will fill in the grid as we learn about its quadrants. Starting with the centralized vs.decentralized axis: centralized custodians include Coinbase, Binance, Kucoin, Kraken, FTX (at one point), and many more. You can think of custodying with these providers like having a bank account: they are companies that users entrust with their assets. They hold the assets in omnibus accounts behind the scenes and require users to reveal their identities and go through AML processes in order to get an account.
The obvious advantage of centralized storage solutions is ease-of-use. Users do not have to be tech-savvy to custody crypto in these accounts, as the user interface is similar to a bank or e-trade account. Login occurs via email and password and the company can be contacted if something goes wrong. That being said, centralized platforms do require users to trust them very heavily, as situations like FTX’s misuse of customer funds and subsequent collapse or platform compliance are entirely dependent on the centralized entity’s behavior. Since reserves have to be held in various different coins, centralized platforms have to be extra careful about how they leverage user funds. It is also common for centralized platforms to lack strong customer service, meaning users routinely get locked out of accounts or find themselves unable to make contributions or withdrawals. Centralized platforms also have less options by way of coins available for exchange and financial engineering because they are heavily regulated. This is ultimately to the benefit of most users, though, as engaging with fringe assets and exchange functions requires a high level of sophistication.
On the other end of this spectrum exists decentralized custody. If centralized custody is a bank account, decentralized custody is cash under your mattress. Let’s review a hypothetical scenario to help differentiate centralized from decentralized platforms. An employee at Coinbase, a centralized custodian, has a lot of avenues to steal user funds if they want to. They can physically change the database recording how much of which assets a user has, they can misappropriate funds like FTX, or they can indiscriminately lock accounts or be unhelpful with account recovery such that after a couple of years, the company gets to absorb those assets. All of this is in virtue of the fact that all ownership and account data as well as the actual assets are fully controlled by Coinbase. Decentralized platforms mitigate all of these risks as there is no centralized custodian. Instead, individual users, called ‘miners’, put up cryptocurrency as collateral in order to run a software program on their computer that verifies new transactions and updates the network’s database. If any one computer incorrectly verifies a transaction, they lose part of their collateral. If they correctly verify transactions, they gain cryptocurrency. ‘Correct’ verification, in this case, means accurate bookkeeping: the computer is not trying to fudge numbers or approve malicious transactions. This is a very brief explanation of what is called a ‘consensus algorithm’: each blockchain employs one and they both mathematically ensure good participant behavior and cryptographically ensure user anonymity and fairness in the system. So, to recap, decentralized platforms do not rely on any single actor and instead allow for fast, trustless transactions with no expensive or slow middlemen.
The second important feature of decentralized networks is how asset custody is managed. Because the network is decentralized, new users who join are given an account that they can login to using a public and private key pair, both of which are not stored anywhere in the network. Think of this like email and password, where the public key can be given out to receive cryptocurrencies, just like an email can be given out to receive messages, and the private key must be kept private as it provides access to the account, like a password. The main difference is you cannot change your password if you lose it: you will be locked out of your account forever. Since decentralized platforms do not have customer service (they are not being run by a company and any ‘profits’ are sent to miners), if a private key is lost the account will be inaccessible. There is no centralized entity available to retrieve your assets. Although this is scary, it eliminates all risk associated with allowing a company to hold your assets. Users also get to use the assets anonymously which can be very good or very bad, but that is for another paper.
All in all, decentralized platforms provide users with great privileges, but also with the great responsibility of safeguarding their private key. Users should never, ever share their private key, as whoever it is shared with can steal all of their assets anonymously in a matter of seconds.
Now that we roughly understand the difference between centralized and decentralized custody, let’s place some providers of each on our grid. In order from top to bottom, Coinbase, Binance, and Kucoin are all centralized cryptocurrency platforms. Below them on the decentralized portion of the axis are Electrum, a popular decentralized wallet on the Bitcoin blockchain, and MetaMask, a decentralized wallet on the Ethereum blockchain.
The access points of centralized and decentralized are completely different and cannot be handled the same way when it comes to estate or financial planning.
Now let’s discuss the second axis, hot vs. cold storage. This simply refers to whether or not the wallet is connected to the internet. In the case of hot storage, the private key is stored locally on the user’s computer, and can be hacked remotely as there is an internet connection to the computer. Cold storage, on the other hand, is not connected to the internet and therefore cannot be accessed remotely. Examples of cold storage solutions include writing your private key down on a piece of paper, using a cold storage hardware wallet (a small USB-type device), or memorizing your private key. These solutions can only be hacked by people in proximity to you: they can steal your piece of paper, hack your hardware wallet, or find a way to get you to reveal your memorized private key. Cold storage is safer than hot storage, but many users still opt for hot storage as it makes trading and interaction with their coins much faster.
Let’s place some examples of hot and cold storage on the grid.
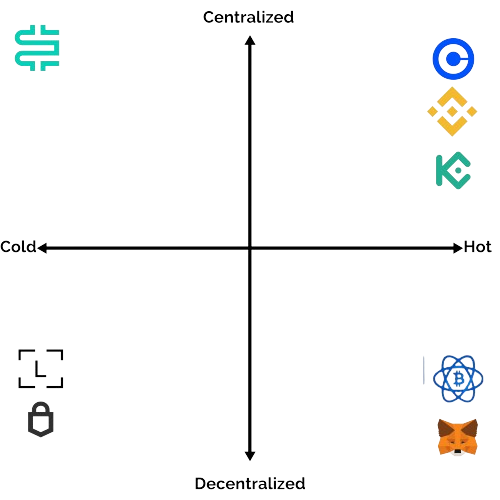
In the top left centralized + cold quadrant is Nydig. Nydig is a custodian that holds all client assets in cold storage. Nydig mainly services very high net worth individuals who are afraid of being physically targeted for having large amounts of cryptocurrency and also want extra assurances on how their custodian is storing their assets.
In the top right centralized+hot quadrant are Coinbase, Binance, and Kucoin, which we have already discussed. It is possible for hackers to remotely access people’s accounts on these platforms.
In the bottom left decentralized + cold quadrant are Ledger and Trezor. These are small hardware devices users can purchase to hold their cryptocurrency offline. Finally, in the bottom right decentralized + hot quadrant are Electrum and Metamask. These wallets are decentralized but keep the private key stored in the user’s computer, meaning it can be accessed by hackers when the device is connected to the internet.
Let’s quickly review! Firstly, a user can store their assets with a centralized entity which forces them to give up their identity, trust that entity, and be bound by the policies of that entity. Instead, they can store their assets in a decentralized fashion and incur the burden of keeping the assets safe. Secondly, they can either store their assets in hot storage, which allows them to use their assets more easily but also exposes them to hackers, or they can place their assets in cold storage which limits hackers to people who can physically access them, but also doesn’t allow them to use their assets as easily.
Now you know how crypto is stored! Asking your clients about digital assets is a great way to ensure they have a comprehensive financial plan in place, and knowing the correct language goes a long way in gaining their trust.